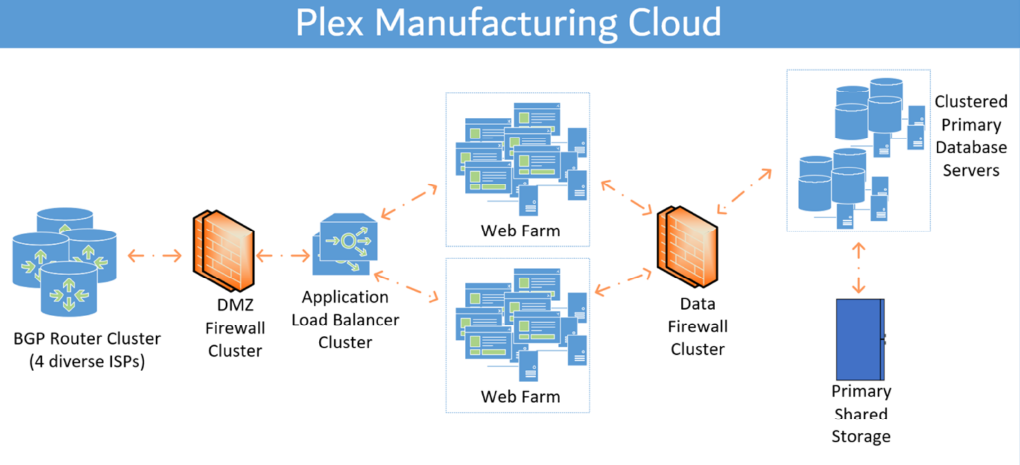
Cybersecurity is a top priority here at Plex. As a cloud-based software service, we treat our responsibility for your data with the utmost seriousness. That’s why we maintain compliance with the most stringent information technology standards. Below you’ll find a detailed breakdown of everything we do to keep your data safe and secure.
Our efforts extend not only to the privacy and security of your data, but also its integrity and availability.
Data
Confidentiality
Only authorized parties have access to your data.
Data
Integrity
Controls are in place to ensure that your data is protected from errors and corruption.
Data
Availability
Network security and availability are built into our platform so you can access your data anytime, anywhere.
Data
Privacy
Private data is identified and protected according to applicable laws, rules and regulations.
We don’t take your trust for granted. It’s the foundation of our partnership together, and it’s why we continue to seek out new cybersecurity standards and certifications to meet.
Check back regularly on this page to learn about the updates we’re making in our mission to serve you better.
Questions? We’re here for you. Reach out to us anytime.